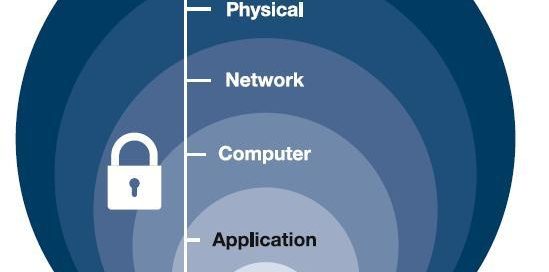
Defense in Depth also known as the Castle Approach is an information assurance concept. It is defined as a concept in which multiple layers of security controls are placed throughout an information technology system. As compared to the Castle Approach one layer of security is simply not enough, the moat will not keep all the attackers away. A Defense in Depth approach can be executed a multitude of different ways but we will be dissecting one method with two main systems. Those two assets are a Geo blocking device, and a unified threat management firewall.
A Geo filter device has a multitude of uses and functions, although its’ main purpose is to stop traffic from going to countries that is not anticipated. As we have all seen in the news, there are many Governing societies around the world that are becoming active in hacking. It is beneficial to block traffic from those countries to enter your network if it is unexpected. This also stands true for a built-in feature of a virus to “phone home”. This traffic will be destined to one of those previously mentioned known malicious countries. This will stop the information from being sent to its destination from compromised systems. Most users are widely unaware of the traffic that is entering and exiting their network. A device like this will provide great visibility and the ability to block any unwanted traffic based on their location.
The second device that is mentioned is a unified threat management device, this will be the second item that will see all the traffic entering and leaving your network. As you may or may not know there are many malicious web sites, click jacking ads, and other malware infested items spread across the World Wide Web. A system that will prevent data and the accessibility into those malicious items is absolutely necessary in any network big or small. A firewall has many tasks, I would like to point out its 2 mission critical tasks as traffic is traversing over your network. As previously mentioned web filtering is beneficial both to prevent the access of malicious items as well as keep productivity in the office at an all-time high. The second main feature is anti-virus scanning. Although, not mentioned here many infrastructures employ a host-based AV scanning system. This system we have mentioned is network based and scans all attachments, and traffic moving on the network. One benefit of this is stopping the attack before it even enters the network. Lastly, firewalls on the market today have a vast array of functions and capabilities but in order to properly secure your network, web filtering and anti-virus scanning are two things you should be looking for as you deploy a firewall.
In conclusion, there are many different methodologies and aspects to look at a Defense in Depth plan. We mentioned a Geo IP filter and a UTM firewall as only two. However, these systems are mere steps in the correct direction to securing proprietary data as it traverses the vast threat landscape that is the internet. Please ask yourself “Could I afford to lose this piece of information?” If the answer is no, then you should be conscious of your network security and placing another layer between you and the attacker.