Modern businesses generate more data than ever before to such an extent that their digital assets are often even more valuable than their physical ones. With IT being critical to many modern business operations, it is imperative that your company has a solid data storage and backup strategy in place to safeguard you in the event of a disaster.
Cyber Crime 101: How to Stay Informed and Defend Your Online Business Accounts Against it

Symantec, a well-known cyber security company, partnered with National Cyber Security Alliance to investigate small businesses and how they are affected by cybercrime. What they found was surprising: 83 percent of these companies have no specific plan in place to protect against cybercrime and 69 percent have no plan at all.
3 Reasons Why Small Businesses Should Migrate to Office 365

Many small businesses have migrated to the cloud, often with mixed results. In the past, the technology wasn't as reliable as it was now. Another weak point was that migrating and adjusting to the change took valuable time.
Microsoft made sure that won't be the case with Office 365.
Microsoft's primary focus is on making the software viable for small businesses.
How Cyber Criminals Use Social Engineering to Hack Businesses
Ransomware: Is your Business at Risk?
5 Essential Tips to Protect Your Small Business Against Cyber Crime

Small businesses have become a prime target for cyber criminals in recent years. The potential rewards are smaller than those available from hacking corporations, but small enterprises are softer targets. A cyber criminal can breach the security systems of hundreds of small businesses in the time it takes to hack the protections of a corporation.
Five Keys to a Successful Managed Service Provider Adoption
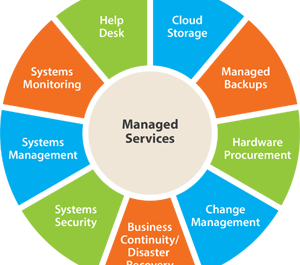
For small-to-mid-sized businesses, adopting an information technology managed service provider (MSP) can be the silver bullet for a multitude of computer and network problems. MSPs operate on a pay-as-you-go, fixed-fee basis, allowing clients to better predict IT services costs and scale their computer and network systems smoothly and easily.
Lowering the Risk of Cyber-crime Starts at the Top

Having an account compromised is both infuriating and terrifying. Someone reaching into your personal information and using it for their own monetary gain is a personal violation most people would rather avoid. Big cyber-attacks on large corporations like Target, Home Depot, and even JP Morgan Chase make many consumers wonder not only if their information can ever really be safe, but also who is really to blame for not ensuring the safety of their accounts.
Six ways to protect yourself from a phishing attack

Phishing is a type of cyber attack in which the attacker attempts to obtain your private information using fraudulent websites and spoofed emails. Typically, a phisher will send a legitimate looking email that claims to come from a company which you have an account with, such as a bank or social network.
15 Tips for Online Safety & Security

With more and more people gaining access to the Internet every day, the importance of ensuring that you and your information remain secure while using the Internet for personal or business reasons cannot be stressed enough. Cyber attacks, viruses, malware, and unwanted intrusions into “secure” computing systems occur frequently and these issues cannot be completely eradicated.



