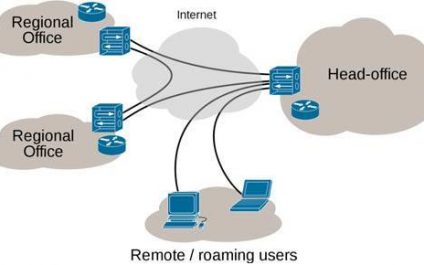
Any business owner who handles sensitive data, especially the kind that is related to their clients, knows how important it is to ensure that no security threats can cause a data leak, since that would pretty much mean the end of their business.
This is why more and more businesses are implementing two-factor authentication.