The number of people working from home continues to surge due to the impact of the COVID-19 virus. Providing employees with the necessary tools to work from home is essential in maintaining productivity during these uncertain times. Network Access can play a key role in helping employees to work from home without jeopardizing data security.
5 Ways Network Access can Help Your Employees Work Remotely
The Homeless Homebuyer
Cyber Security Awareness Training that is actually engaging and entertaining!
Watch a sample video by clicking this link: The Homeless Homebuyer by NINJIO.
NINJIO is an I.T. Security Awareness training company focused on engaging end users. In short, they produce 3-4-minute-long animated story based episodes featuring real security incidents that educate by engaging employees about the dangers that exist in cyber security.
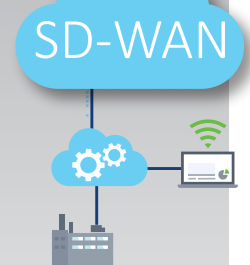
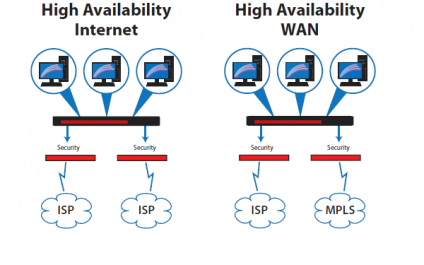
SD-WAN: Fast and Reliable Internet/
WAN Connectivity are Critical
For many organizations, slow internet or loss of connectivity can often be a major business impacting situation.
We all are relying on Internet or WAN connectivity more for mission critical applications such as email, web access, chat, video training, cloud applications and VoiP.
Professionally customized for your business needs
NetWatchman SD-WAN will keep your internet and WAN always on and optimized to the highest level of performance to keep your critical applications fast and available.
110 Nursing Homes Crippled in Cloud Ransomware Attack Demanding $14 Million

On Nov. 17, 2019, a Ryuk ransomware outbreak plagued a Wisconsin-based IT company, Virtual Care Provider Inc. (VCPI), according to KrebsOnSecurity, founded by journalist and investigative reporter Brian Krebs.
Around 1:30 a.m. on the day of the attack, unknown hackers launched a ransomware strain known as Ryuk inside VCPI’s networks.
Ransomware Demands Skyrocket
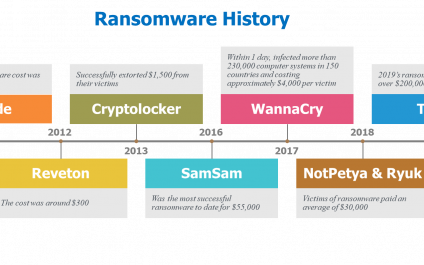
GREEDY CYBER CRIMINALS AND THEIR RISING COSTS
It doesn’t seem that long ago that ransomware attacks became a premier choice for hackers and scam artists. One attack I vividly remember from the early days of ransomware was around 2012, when we helped a local Pittsburgh client with a locked-up computer that had been frozen with ransomware.
Superhero or Single Point of Failure?

The Dangers of Asking Your Sole IT Support Technician to be Your Superhero
As the old saying goes, “Hope is not a strategy.” But for many organizations, hope is the strategy when it comes to their technical support staffing.
At a large number of organizations, IT staff members are often asked to take on “superhero support” measures to keep the applications available 24/7. This could mean they work late nights and into the early morning to maintain the company’s critical functioning systems and drag themselves into work the next day.
What Are Managed Service Providers and How to Choose One for Your Business?

Managed Service Providers (MSPs) are a new option for technical support and systems administration for businesses who do not have information technology management in their core competencies. MSPs typically offered fixed-fee for services solutions to manage SMB computer systems and provide on-demand technical support.
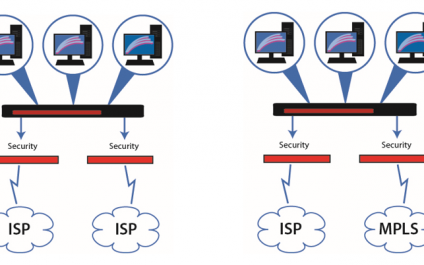
What is SD-WAN?
How To Improve Cybersecurity In Your Business
SD WAN
Organizations have become so dependent on technology that when applications become unavailable, we often see employees pack it in and go home for the day.
Most all organizations have become extremely technology centric relying on the availability of business critical cloud/SaaS applications, email, voice/video collaboration, web access and more.